New Cybervirus
Last Monday Kaspersky Labs posted a security report on its website, saying that a new cyberspy campaign has been uncovered, and its scope is something we haven’t quite seen before. The new cyberspy virus has been called “Red October” after Tom Clancy’s novel, and the new cyber threat is no less dangerous than the fictitious Typhoon class submarine. According to Kaspersky, Red October has been out trying to steal critical information since 2007 at the least. Judging from its encryption scheme, Red October is aiming for NATO and other governmental agencies data bases. What is more, it can also steal information from mobile phones, and reinstall itself automatically on the machine, if it has been removed.
Red October origins
Kaspersky did not reveal the source of the virus nor the organizations that have been attacked by it. However, based on the fact that the firm is cooperating with the cybersecurity arm of the U.S. government for this research, we can tell that the investigation is given an utmost priority. Unlike other computer infections nowadays that aim for high infection rates to generate big revenue, Red October is targeting only several high-value targets. Kaspersky says that Eastern Europe and former Soviet republics are the most susceptible to the attacks. However, unlike other big cyberspy virus (like Flame, for example), Red October does not seem to be an instrument of geopolitics. Rather than that, the hackers behind this virus seem to be motivated by high-profit, because sensitive data stolen from governmental organizations could be sold for a very high price underground.
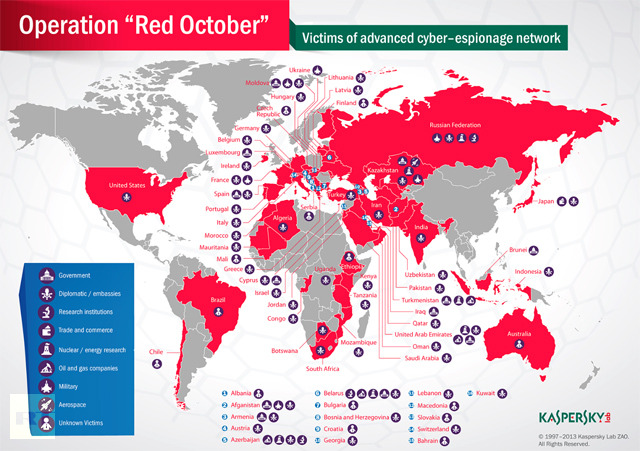 source:http://rt.com/news/red-october-cyber-attack-network-000/
source:http://rt.com/news/red-october-cyber-attack-network-000/
Virus structure
Red October takes parts of its structure from previous notorious infections. It has a code from spear-phishing emails that are used to infect specific single users. Other codes have obviously been taken from Chinese hackers and the infamous Conficker worm that is notorious for its ability to control infected machines.
The command prompt of the virus is issued in Cyrillic fonts – these fonts are used for Cyrillic alphabets utilized in Russia and other Slavic languages. However, Kasperky says that is not the reason to believe that Red October has been created and distributed by Russian hackers.
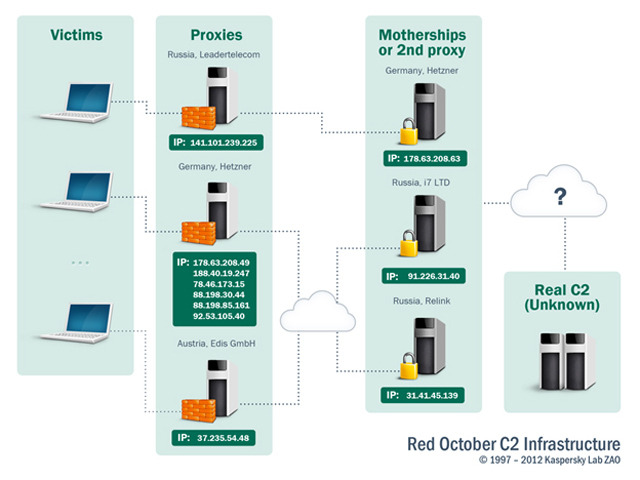
Source:http://rt.com/news/red-october-cyber-attack-network-000/
Unique characteristics
The cyberspy virus is unique in a way that its behavior suggests it has been created for wide espionage campaign. Since it can infect smartphones, once Red October gets into a target computer it automatically searches for a smartphone device connected to the computer in order to spread further. It can also scan and infect plugged USB drives, ready to steal any information that is stored in a USB thumb drive.
Cyberwarfare
Digital espionage has been long predicted by security specialist and the discovery of Red October does not come as a big surprise. Although it might not be as dangerous the Flame virus, it still can resurrect the files that have been deleted from USB drives, and as a result it creates more challenges for security specialists. What is surprising, however, is that Red October managed to get that far, because its tactics is not by any means subtle. At least we’re lucky this cyberspy virus has been discovered and revealed to the public.
Source: http://www.networkworld.com/



0 Comments.